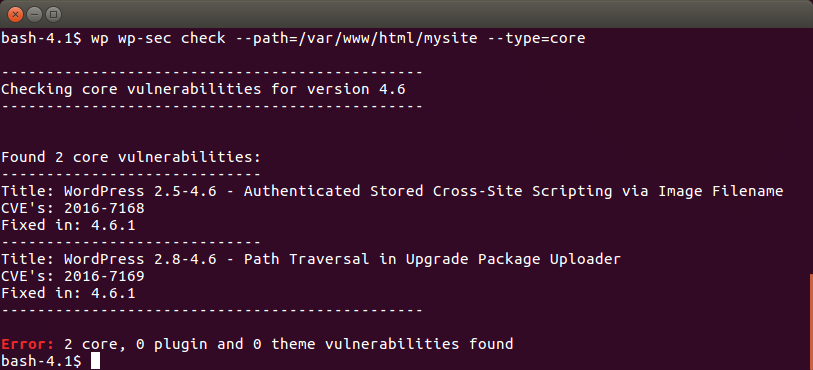
Below is the synopsis of the wp-sec package
SYNOPSIS
wp wp-sec <command>
SUBCOMMANDS
check Checks for core, plugins and themes
version Returns current version
CHECK PARAMETERS
--type=[core|plugins|themes|all]
Check for a specific part, or use all to check all parts
Default: all
--output=[user|nagios|json]
Controls the output
Default: user
--cached
Lets you cache the resuls of wpvulndb, to prevent hammering at their servers. Be nice to them, it's a free service
--ttl=[integer]
Cache control of above --cached setting. If omitted a default of 8 hours is used. This setting will give
you fine grained control. Value is entered in seconds
--api=[v2|v3]
The WPvulnDB API version to be used. Currently there is no functional difference between these API's. Except for logging in with a token on API v3
--token=[<your token>]
Your user token to be used @ wpvulndb.com. Only needed for API v3
--lowercase
Converts themes and plugin names to lowercase to submit to wpvulndb. This is due to an issue at wpvulndb. https://github.com/markri/wp-sec/issues/14 As of october 2018 (tested) it doesn't seem to be needed anymore
GLOBAL PARAMETERS
All global wp cli parameters are inherited
Please use this scanner with a decent interval. I was informed about a limit of 30 calls every 30 seconds. Thus: a site with 1 core, 1 theme and 10 plugin is already 12 calls
Example command; a Wordpress site is checked just for core vulnerabilities at given path (inherited option from wp-cli)